Rhizomes and Social Networks –
This week’s readings bring us around to the rhizome analogy, one which Deleuze and Guattari wax philosophic over (when they apparently are indulging in some pharmaceutical hallucinations, I gather). Their rhizomatic illustrations seem to serve as a useful hinge upon which to balance Scott’s article that narrates the building blogs of an evolving system of theory, and that of Rainie and Wellman’s anecdote-filled discussion of the Third Revolution.
I read Scott first, in preparation for our Tree collaboration, and found it especially helpful in terms of the way it moved the reader relatively smoothly through a narrative of who was building upon whom. Interestingly, his self-proclaimed purpose is to “bridge [the] gap between theory and practice” (1), something many of our “show and tell” build projects seem designed to do as well. (Frankentheorists Anonymous.) His focus is on “social network analysis” (1) for the purpose of “identifying…key concepts” and finding “kinship patterns” (1-2), a useful foundation for the next two readings of this set, as he provides some useful pragmatic elements as balance to Deleuze/Guattari’s more ideological treatise, and as well to inform the analogous turn of Rainie and Wellman. Several key terms of note:
- Attribute data = “attitudes, opinions, and behaviors” that serve as “characteristics” of individuals and/or groups (2).
- Variable analysis= a way to measure the “values of particular variables” like “income, occupation, education” (2).
- Relational data = “the contacts, ties, and connections…which relate one agent to another and [what seems most important] cannot be reduced to the properties of the individual agents” (3). He asserts that this is key to the social sciences in that it highlights the focus upon “the structure of social action,” not simply the individuals (4).
- Ideational data = describes the “meanings, motives, definitions and typifications themselves” (3)
He cites three main lines of development of analysis: sociometric & graph theory, dealing with small groups; cliques or “cohesive sub-groupings” (16); and anthropologists / networks (26). Interestingly all three claim to build upon the other, but differentiate by shifting the focus of outcomes in varying directions, largely based on the perception of scaling the cause-effect. The graph theory raises the ever-important element of research, and that is the influence of the group upon “individual perceptions” in terms of how social organizations inform the system a the very basic level of the “I” (8-9). Scott points to the usefulness of sociometrics in creating “analytical diagram[s]” such as what researchers often use to map data: graphs, bar charts, etc. (10). He presents a variety of different diagrams other than basic lines that graph networks of behavior in terms of relationships (13) in structural terms that sound a great deal like the networks we’ve been exploring to date. His nod to interdisciplinarity as a strong influence in determining such representations struck a chord with me, thinking of ways we’ve been drawing upon any number of fields to make connections to English Studies. (I’m often surprised to see how well they fit!)
I appreciated his article’s focus on making analysis accessible, and for his advice on what potholes we need to avoid when theorizing any analysis – like forced applications. That seems to be a risk whenever working with metaphors – there is always something that doesn’t quite fit. Enter: FrankenTheory. Where one analogy fails, we usher in a second (or a third) as a layering system of interpretive tools. His cautions are clearly well-founded. I especially appreciate his observation in Chapter 3 that one of the risks of “construct[ing] sociograms” is their tendency to obscure the important smaller nodes of connections – masking the trees in the larger scale of the forest (40). I was painfully aware of my wildly out-of-control Mind Map at this point – in anticipation of the need to restructure it by theme. (I wondered if that directed activity is intended as an offshoot of Scott’s observation here!)
Scott brings us back to the notion of boundaries in Chapter 3, observing: “What these problems point to is the fact that the determination of network boundaries is not simply a matter of identifying the … obvious boundaries of the situation.” That’s because locating or naming said boundaries in research “is the outcome of a theoretically informed decision about what is significant in the situation under investigation” (54). As Dr. Romberger pointed out recently, our research will inevitably require us to be transparent in recognizing our biases as part of our analysis.
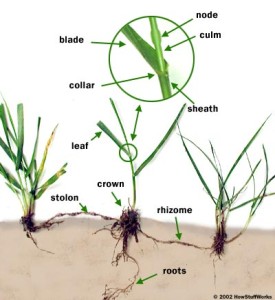
Next in the order of things comes – in my scheme of things, at least – Deleuze and Guattari’s treatise on rhizomes. I find their conceptualization of this physical schema especially useful as an alternative to a more traditional linear mapping of relationships and networks. Their attention to the characteristics of a rhizomatic form (grass-like) vs. an arborescent (tree-like) form became a bit of a mantra when our group was designing our theory lineage line. Especially helpful was their delineation of characteristics, again opening up possibilities for transferring to discussions of our Objects of Studies. The non-genetic nature of rhizomes seems to suggest that thinking of theories evolving out of previous theories overly simplistic, that such hierarchical imagery too often leaves out the multi-directional influences of other networks (cultures, individuals, etc.). This clearly gels with so many of our other theorists (Castells and Latour, most recently) who argue that we must see network influences happening in a multi-directional format – again, thinking back to Dr. Romberger’s asterisk when explaining ANT.
I found their commentary on Eastern vs. Western cultural thinking especially note-worthy, and in particular their suggestion that American cultures manage to blend both in many ways. Perhaps this has more to do with the “age” of a culture than ethnocentricity, with a culture of immigrants – blending a myriad of histories and cultures – creating a multi-nodal sense of identity.
There is one concept that I must confess I have not quite wrapped my brain around – maps and tracings…that tracings must be put on the map, not the other way around (21). Perhaps, like Winnie the Pooh, I need to go to my Thinking Spot and ponder that for a time.
Finally, Rainie and Wellman cap off this trio by placing these ideas of rhizome connections and data collecting in the context of the age of mobile communications networks. I must confess, thinking of our culture and communities as an OS – not unlike Maverick from Apple or (ugh) Windows 8 – is one I’m not entirely ready to embrace. Clearly, Rainie and Wellman resist the argument that our age of cell phone-networked cultures is creating isolationists. And while they do give a nod toward some of the downsides of the mobile-technology obsessed, I did get the sense that they are firmly in the cheer camp of “more mobile is good for us.” (Would this mean the meme above could be rendered as a Zombie Rhizome?)
Their distinction between networked versus embedded remains a bit fuzzy to me. They seemed to go to great lengths to clarify the notion of individuals networked vs. embedded into groups, pointing out ways in which mobile communication technologies allow for greater, rhizomatic growth beyond a spatially limited contact list. They clearly want us to see this in terms of social groups problem-solving by outreach and information gathering efforts. At the heart of this is what they call “three revolutions”:
- The social network revolution – extending the social circle beyond proximity and traditional family / village units;
- The internet revolution – increased communication and knowledge gathering powers; and
- The mobile revolution – creating “appendages” to our physical bodies for the purpose of making connections unencumbered by time or space (even referring to Castells’ “space of flows” on page 102).
These three revolutions are mutually influential “in the network operating system” (107), in good and bad ways. I laughed when they pointed to the examples of “present absence” (103) in an image of teenagers sitting in the same room engaging with each other through mobile devices rather than face-to-face interactivity. Or the public space invading private space in the case of cell phone conversations in public – I think we’ve all been a part of that.
But what makes this a “revolution,” exactly? Is this, in some ways, enthusiastic hyperbole? If we define revolution as “no turning back” change, then yes – the impact of communications technologies on our social interactivity is revolutionary. Is it rhizomatic? Yes, I think so, certainly given the ways in which these authors talk about individuals’ abilities to expand outside of their geographically located spaces and branch out into new networks at will, even jumping past traditional bridges (thinking here of Facebook’s Friend features as a “partial membership in multiple networks” — 12) to move into new realms of connections – the “Connected Me” (19). Such technology also shatters traditional (or else, long standing) boundaries such as work / home, public / private, and aligns with Deleuze and Guattari’s description of the rhizome beginning in the “middle” and not the ends (21), rupturing at “segmentary” points along the line yet still remaining connected (9). Could this be possible with any other technology other than Internet-linked channels?
The principal characteristics outlined on page 21 is quite useful when using a rhizome as analogy – it stands apart in many ways from an ecology, or a neurosystem of the brain. It appeals to the controlled chaos theory mentioned in Castells as well, but seems to offer some troubling qualities (like having neither subject nor object) that may make it unwieldy if combining it with a discussion of rhetorical spatial features (thinking here of the MOOC) – that is, of course, unless I weave in ANT.
In summation, I have to end with a reference to the graphic at the beginning of Chapter 1 in Deleuze/Guattari. My house is full of musicians, so staff paper is familiar to me. And when I first spotted the graphic I was reminded of what my book of blank music staves looked like in the hands of a two-year old with crayons. I did not at first spot the rhizome. In fact, I’m still not sure I do. But if we’re talking about the difficulties in crafting visual representations of data from a highly complex subject that seems perpetually in motion (in terms of theorizing, anyway), then yes. I can see it. Or maybe it’s just the Rorshach representation of our overflowing minds at the end of a very busy semester.
Works Cited:
Deleuze, Gilles and Felix Guattari. A Thousand Plateaus: Capitalism and Schizophrenia. Trans. Brian Massumi. Minneapolis: Univ of Minnesota Press, 1987. Chapter 1 only
Rainie, Lee and Barry Wellman. Networked: The New Social Operating System. London: MIT Press.
Scott, John. Social Network Analysis: A Handbook 2nd ed. Los Angeles: Sage, 2010. Chs. 1-3.